Here is a sneak peek to VoIP encryption, SIP, TLS, and SRTP – exploring the threats to unencrypted calls, the importance of VoIP encryption methods, and how choosing the right VoIP encryption protocol can protect against cyberattacks, with real-world examples and essential facts. Stay secure with insights into end-to-end encrypted VoIP and HIPAA compliance!
Ever feel like someone might be listening to your phone calls?
No, it’s probably not the government – it’s hackers!
And if you’re using VoIP without encryption, you might as well be broadcasting your conversations on a loudspeaker.
Let’s be real – in today’s world, privacy isn’t a luxury – it’s a necessity.
🗣 What is VoIP and Why Does Its Encryption Matter?
VoIP (Voice over Internet Protocol) is basically the digital evolution of traditional phone calls. Instead of old-school copper wires, it transmits voice data over the internet. It’s cheap, efficient, and flexible – but here’s the catch – anything traveling over the internet is fair game for hackers unless properly secured.
Imagine discussing confidential business plans or sharing personal details on an unencrypted VoIP call. Without the right VoIP encryption methods, cybercriminals can intercept and exploit this data. That’s where encryption comes in – locking down your conversations to ensure your voice stays yours.
The first VoIP call was made in 1973 by Dr. Martin Cooper, the inventor of the mobile phone, using a system called “The Internet Protocol.” It wasn’t until the 1990s that VoIP technology became mainstream.
What are the Threats to Unencrypted VoIP Calls?
Leaving your VoIP calls unprotected from VoIP potential threats is like leaving your front door wide open in a bad neighborhood – anyone can waltz in. Here’s what can happen if your calls aren’t secured:
🗣 Eavesdropping
Ever get that eerie feeling someone’s listening in? With unencrypted VoIP calls, they probably are! Hackers can tap into your conversations, stealing personal or business info. If you want an encrypted VoIP service, encryption is your best defense.
🗣 Man-in-the-Middle Attacks (MITM)
Picture this: you’re on a call with a colleague, but what if a hacker secretly intercepts the conversation, alters messages, or even impersonates you? Without solid VoIP encryption protocols, your private discussions could turn into someone else’s playground.
🗣 DDoS Attacks
Your encrypted VoIP phone suddenly goes silent in the middle of an important call. Why? Attackers flood your VoIP network with junk traffic, making it unusable. A strong VoIP encryption method coupled with network security can help prevent these attacks.
🗣 Phishing
It’s not just about sneaky hackers; sometimes, they trick you into giving them access. Fake emails, deceptive links, and social engineering tactics can steal login credentials and compromise even the most end-to-end encrypted VoIP systems.
🗣 Malware & Viruses
Unsecured VoIP systems are just another entry point for malware. Cybercriminals can inject malicious software to spy on your calls or even take over your system. An open-source encrypted VoIP solution with strong security measures is a smart way to stay ahead.
🗣 Wangiri Fraud
Ever had a missed call from an unknown international number? That’s Wangiri fraud. Call back, and you could be racking up insane charges. While encryption won’t stop Wangiri scams, a properly secured encrypted VoIP service can help detect and block fraudulent activity.
The bottom line? If your VoIP isn’t encrypted, you’re rolling out the red carpet for cyber threats.
📱What is VoIP Encryption?
Encryption in VoIP works by converting voice data into a secure format that only the intended recipient can decode. Think of it as your private call getting wrapped in an unbreakable digital vault while traveling across the internet.
Here’s how encryption shields you from the threats above –
👉 Eavesdropping? Blocked.
Encryption scrambles your voice data, so hackers can’t make sense of it.
👉 MITM Attacks?
No chance. Secure protocols verify both parties before establishing a connection.
👉 DDoS Attacks? Minimized.
Encrypted connections reduce vulnerability to brute-force attacks.
👉 Phishing? Tougher to exploit.
Strong security frameworks make stealing credentials harder.
👉 Malware? Stopped at the gate.
Secure VoIP setups prevent unauthorized software from sneaking in.
👉 Wangiri Fraud? Detectable.
Advanced encryption-based fraud monitoring can spot and block scam numbers.
According to Cisco, businesses that switch to VoIP can reduce their carbon emissions by up to 70% by eliminating the need for physical infrastructure like copper phone lines and data centers. VoIP’s internet-based communication model is helping companies reduce both costs and environmental impact.
According to Cisco, businesses that switch to VoIP can reduce their carbon emissions by up to 70% by eliminating the need for physical infrastructure like copper phone lines and data centers. VoIP’s internet-based communication model is helping companies reduce both costs and environmental impact.
Now, let’s talk about the three main superheroes of VoIP encryption: SIP, TLS, and SRTP.
How confident are you that your VoIP calls aren’t being intercepted right now?
📱What is SIP?
SIP (Session Initiation Protocol) is the backbone of any VoIP system. Think of it as the digital “bouncer” at the door of your phone system – it handles the signaling process, ensuring that calls can be set up, maintained, and terminated. When you make a call, SIP is responsible for everything from dialing the number to establishing the connection and even ending the call.
However, here’s where it gets tricky – SIP, by itself, doesn’t offer encryption. In other words, it’s like having a bouncer who lets anyone walk in without checking their credentials. This leaves your communication open to vulnerabilities, such as eavesdropping, call hijacking, or impersonation.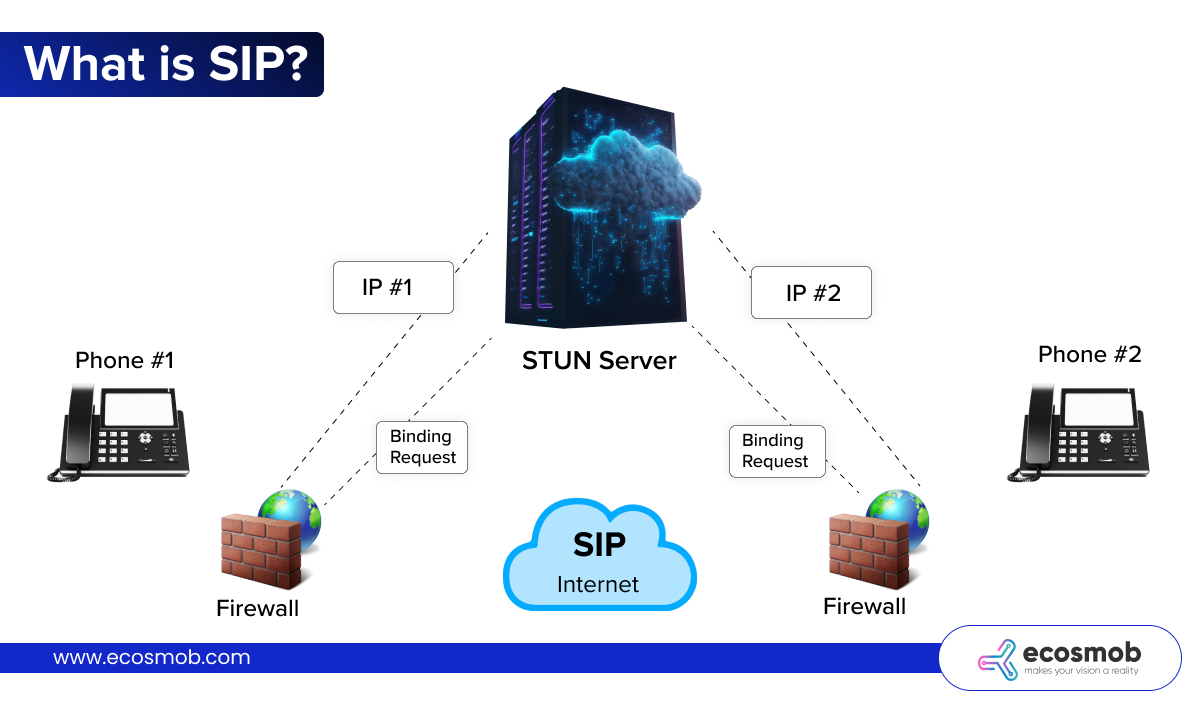
For example, a hacker could intercept your SIP messages to figure out when you’re making a call or even hijack the call to gain unauthorized access to your conversation. That’s why using SIP encryption is a must if you want to secure your VoIP system from these attacks.
So, how do we fix this? That’s where TLS (Transport Layer Security) comes in.
How TLS (Transport Layer Security) Encrypts SIP Traffic?
Enter TLS, the protocol that saves the day! Think of TLS as the high-tech security system you add to your SIP setup. It encrypts the signaling messages (the setup and tear-down of calls) to ensure they can’t be tampered with or intercepted by malicious actors.
Why is this so crucial? Here are a few reasons why TLS encryption is a game-changer for VoIP:
- Stops Eavesdroppers – Without TLS, anyone with the right tools could snoop on your SIP messages. TLS ensures that the data between you and your destination is encrypted, so hackers can’t easily decipher your communication.
- Prevents Call Hijacking – Call hijacking is a real risk with unprotected SIP. This means an attacker could take over your call after it’s been set up. With SIP TLS encryption, you’re ensuring that no one can secretly join or manipulate your conversation.
- Secures Your Identity – Your SIP messages contain identifying information (like IP addresses, phone numbers, and caller IDs). With TLS, all of this data is encrypted, making it much harder for hackers to track or impersonate you.
In short, TLS ensures that your SIP communication is secure, which is especially important when dealing with sensitive business or personal data. Without it, VoIP encryption is incomplete, and your calls are at risk.
Think your VoIP calls are private? 94% of cyberattacks start with unprotected communication!
How does SRTP (Secure Real-Time Transport Protocol) Protect the Voice Data?
While TLS secures the setup and signaling process of your VoIP call, SRTP steps in to protect the actual voice data. After all, the real reason you’re using VoIP is to talk to someone, right?
You want your voice to remain private, and SRTP makes sure it stays that way.
Think of SRTP as the encryption protocol for the conversation itself. Without it, the audio packets (the data that makes up your conversation) could easily be intercepted by a hacker. And if that happens, your private conversation could be played back, analyzed, or even altered.
Here’s how SRTP locks down your voice data:
- Encrypts Voice Data – SRTP ensures that no one can eavesdrop on your call by encrypting the audio. This way, even if someone intercepts the data, it’s just a jumbled mess – no one will be able to hear your conversation.
- Authenticates the Speakers – SRTP doesn’t just encrypt the voice data; it also checks that the person on the other end of the line is who they say they are. This prevents “man-in-the-middle” attacks, where hackers impersonate someone to steal information or manipulate the conversation.
- Protects Against Tampering – Imagine having an important call where someone subtly changes your words – scary, right?
SRTP ensures the integrity of your conversation by preventing tampering. If someone tries to alter the voice data in transit, SRTP catches it and blocks any unauthorized changes.
In essence, SRTP provides the layer of security needed to protect the voice data of your calls. It’s like a lock on the door to your conversation, preventing unwanted guests from listening in or interfering.
How do SIP, TLS, and SRTP Work Together?
When combined, SIP, TLS, and SRTP provide comprehensive protection for your VoIP calls. Here’s how they work in harmony:
- SIP sets up the call, establishes the parameters, and ensures both parties are ready to talk.
- TLS secures the SIP signaling, encrypting the call setup information to ensure no one can intercept or manipulate it.
- SRTP protects the actual voice conversation, making sure that the audio data is encrypted and secure from eavesdropping, tampering, or interception.
Together, these three protocols make sure your VoIP calls are encrypted from start to finish, ensuring that both your setup and conversation stay private and secure.
Does HIPAA Require VoIP Encryption?
If you’re working in the healthcare industry, you’ve likely heard of HIPAA (Health Insurance Portability and Accountability Act). HIPAA is all about protecting sensitive patient information.
So, does HIPAA require VoIP encryption?
While HIPAA doesn’t explicitly require VoIP encryption protocols like SIP, TLS, or SRTP, it does mandate that all communications containing protected health information (PHI) be secure. This means you must take extra steps to ensure the confidentiality of patient data during electronic communication.
Using an encrypted VoIP service that includes SIP, TLS, and SRTP ensures that your calls are protected and compliant with HIPAA regulations.
So, if you’re in healthcare, make sure you’re using a VoIP encryption protocol that meets both your privacy and regulatory needs.
Is saving a few bucks on VoIP worth the risk of exposing sensitive business data?
Choosing the Right VoIP Encryption Solution
If you take security seriously, consider an open-source encrypted VoIP solution. Open-source options give businesses full control over encryption settings, allowing them to tailor security measures to their needs. A provider that offers strong VoIP encryption methods ensures you’re not leaving any back doors open for hackers.
When choosing an encrypted VoIP service, look for:
- End-to-end encryption – Ensures that no one, not even the service provider, can access your calls.
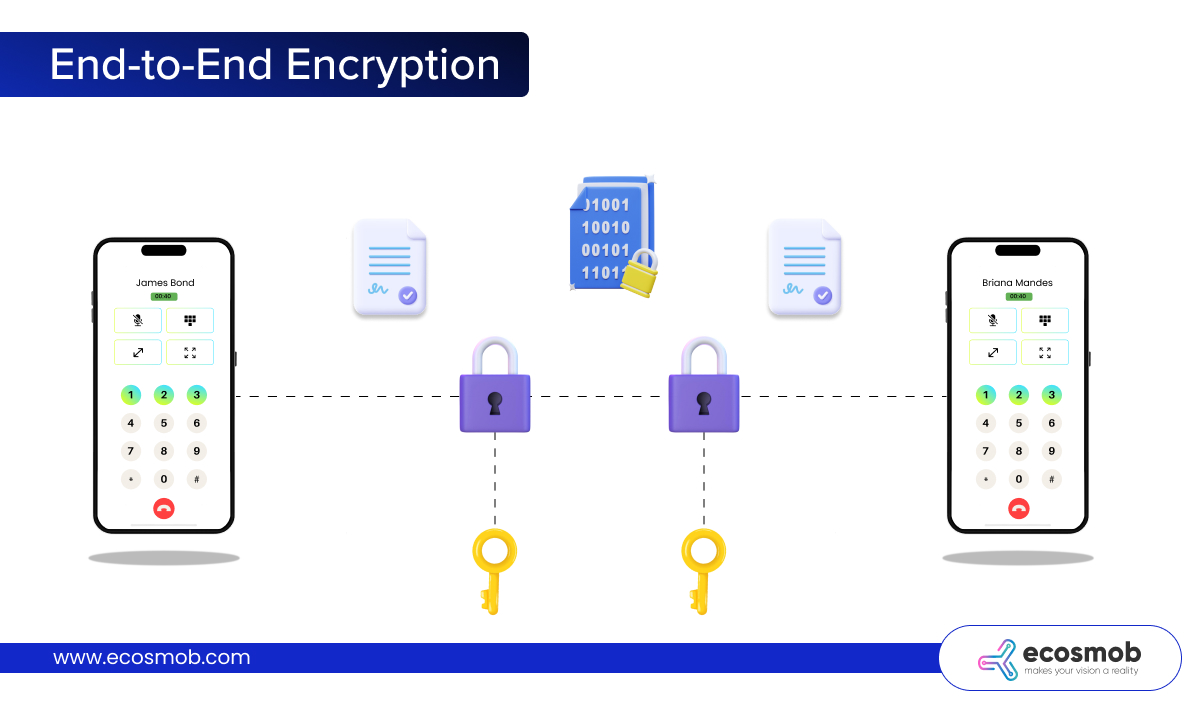
- TLS and SRTP support – These protocols should be standard for securing both call setup and voice data.
- HIPAA or compliance-ready solutions – If you handle sensitive data, make sure your provider meets regulatory standards.
- Regular security updates – Cyber threats evolve, and your VoIP encryption should keep up.
- Multi-factor authentication (MFA) – An extra layer of security to prevent unauthorized access.
Ecosmob Technologies not only provides highly secure VoIP encryption protocols but also customizes security features according to business needs. Whether you require end-to-end encrypted VoIP for internal communication or a secure SIP trunking solution for customer interactions, Ecosmob ensures your conversations stay private and protected because, VoIP encryption isn’t just about privacy – it’s about protecting your business, your clients, and your reputation. Choose wisely!
Wrapping Up
So, is VoIP encrypted? The answer depends on whether you’ve taken the right security measures. If you’re still using an unencrypted VoIP service, your calls are vulnerable to interception, fraud, and cyberattacks. However, by implementing SIP with TLS and SRTP, you can keep your conversations private and secure.
To wrap things up –
- VoIP calls without encryption are an open invitation for hackers.
- SIP manages VoIP calls but needs extra security.
- TLS encrypts SIP traffic to protect call setup details.
- SRTP secures actual voice data to prevent eavesdropping.
- HIPAA compliance requires secure VoIP communication in healthcare.
So, are you still risking it with unprotected calls, or is it time to switch to a fully encrypted VoIP service?
Your privacy is worth it!
What is VoIP encryption?
VoIP encryption is the process of securing voice data as it travels over the internet, making it unreadable to unauthorized users. It uses VoIP encryption protocols like TLS and SRTP to prevent eavesdropping, hacking, and data tampering.
What is SIP in VoIP?
SIP (Session Initiation Protocol) is the technology that sets up, manages, and terminates VoIP calls. However, it wasn’t designed with security in mind, which is why SIP TLS encryption is needed to protect call setup details.
How does TLS protect VoIP calls?
TLS (Transport Layer Security) encrypts SIP traffic, ensuring that hackers can’t see or manipulate call setup details. It prevents call hijacking and ensures that metadata remains private.
What is SRTP and why is it important?
SRTP (Secure Real-Time Transport Protocol) encrypts the actual voice data in VoIP calls. Even if someone intercepts the call, SRTP ensures they can’t decipher the conversation.
Does HIPAA require VoIP encryption?
While HIPAA doesn’t specifically demand VoIP encryption protocols, it does require healthcare providers to protect patient information in electronic communications. Using an encrypted VoIP phone with TLS and SRTP is highly recommended for compliance.


