This blog explores the essentials of Kubernetes network security, with a deep dive into Ingress Controllers and their role in safeguarding your cluster. Readers will gain actionable insights and best practices to effectively secure their Kubernetes environments from real-world threats.
Ever wondered how something as powerful as Kubernetes can be both your greatest asset and your biggest security challenge?
In the ever-evolving world of containerized applications, Kubernetes has become the de facto standard for orchestration. But with great flexibility comes great responsibility, especially when it comes to Kubernetes network security. From traffic routing to access controls, securing your Kubernetes cluster isn’t just a best practice anymore, it’s a necessity.
In this post, we’ll walk through –
- What Kubernetes is,
- Why is network security critical?
- What vulnerabilities do you need to watch out for, and
- How Ingress Controllers play a pivotal role in tightening your cluster’s defenses.
Before we dive into the security challenges and solutions, let’s take a step back and understand what Kubernetes really is and why it has become such a critical part of modern infrastructure.
Not sure if your Ingress Controller is protecting or exposing your apps?
What Is Kubernetes?
Kubernetes, often abbreviated as K8s, is an open-source container orchestration platform designed to automate deploying, scaling, and managing containerized applications.
Instead of managing individual containers manually, Kubernetes allows you to define a desired state, and it works to ensure your application meets that state, even if nodes fail or workloads scale unexpectedly.
A Kubernetes cluster typically includes a control plane and a set of worker nodes. Applications run inside containers that are grouped into pods, which are scheduled on nodes. Kubernetes abstracts away infrastructure concerns, making it easier to build resilient and scalable systems.
While Kubernetes Ingress Controller offers unmatched scalability and flexibility for modern applications, its architecture introduces unique security challenges that can’t be overlooked. Let’s explore why securing your Kubernetes environment is absolutely essential.
Why Kubernetes Network Security Matters | Top 5 Reasons
Kubernetes has revolutionized the way modern applications are deployed and scaled. But with this agility comes an equally complex security landscape. When you’re orchestrating hundreds (or even thousands) of containerized workloads, overlooking Kubernetes cluster security can expose your infrastructure to critical risks.
Security isn’t just an afterthought! It needs to be embedded into every layer of your Kubernetes environment, especially the network.
Let’s explore why securing Kubernetes is not optional but essential –
1. Dynamic and Ephemeral Workloads
Unlike traditional servers, Kubernetes pods are short-lived and can be spun up or terminated rapidly. This dynamic nature makes it hard to apply static security rules, and without a solid Kubernetes network security policy, attackers can exploit brief gaps in enforcement.
2. Broad Attack Surface
Kubernetes clusters involve multiple components, API servers, etcd databases, controllers, kubelets, and more. Each component offers a potential entry point. Misconfigured roles or over-permissive network settings can allow attackers to move laterally through the cluster with ease.
3. Service-to-Service Communication
Kubernetes allows all pods to talk to each other by default. While this eases development and scaling, it introduces risks. An attacker gaining access to one pod could potentially pivot to others, especially if network segmentation isn’t enforced.
Kubernetes was originally designed by Google engineers who had already been running containers at scale internally with Borg. The name “Kubernetes” comes from Greek, meaning “helmsman” or “pilot”, so yes, it’s literally the captain of your container ship!
Many organizations run multiple applications or business units on a shared cluster. Without strict Kubernetes network security best practices, it becomes easy for one compromised workload to interfere with another.
5. Exposure to the Public Internet
With Ingresses, Services of type LoadBalancer, and external DNS, clusters often expose resources to the outside world. Without proper Kubernetes Ingress Controller security, APIs or services might be unintentionally exposed, inviting external threats.
Now that we understand why securing Kubernetes is critical, it’s equally important to recognize the specific threats that target its network layer.
Let’s dive into the vulnerabilities you need to watch for in a Kubernetes environment.
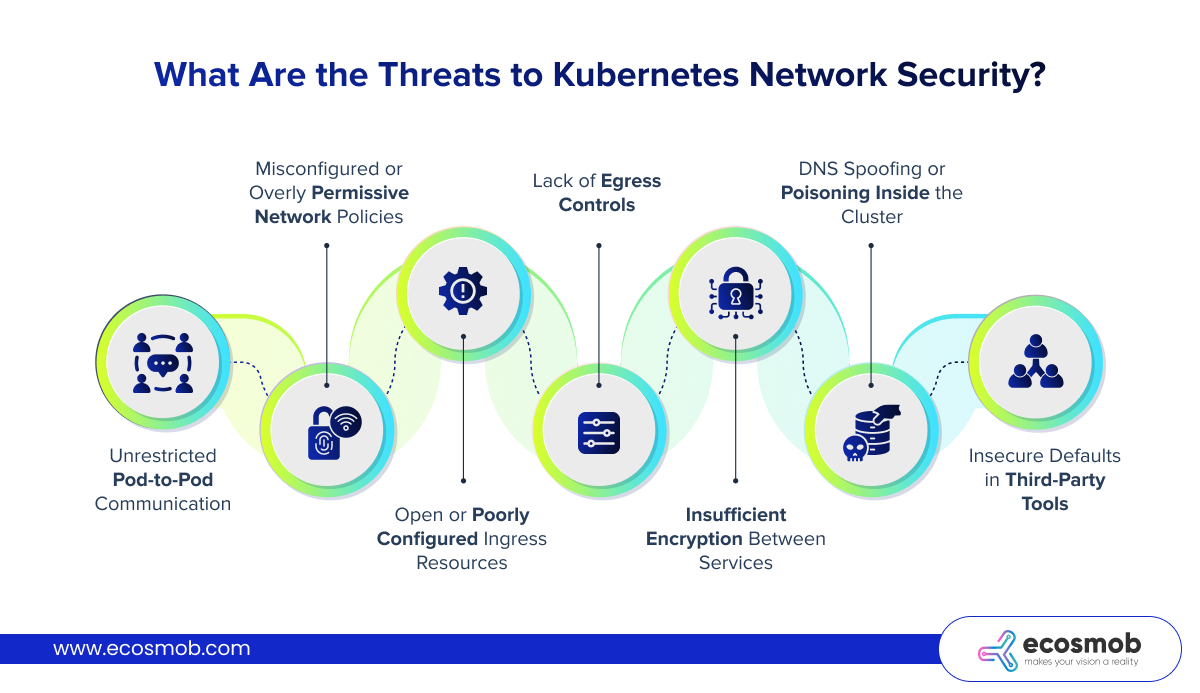
What Are the Threats to Kubernetes Network Security?
Securing a Kubernetes cluster means confronting a wide range of network-level threats. These threats are particularly tricky because of Kubernetes’ default networking behavior: open communication between pods and minimal restrictions on ingress or egress traffic. Attackers often exploit these defaults, especially in clusters that haven’t adopted a strong Kubernetes network security policy.
Here are the major threats you need to be aware of –
1. Unrestricted Pod-to-Pod Communication
By default, Kubernetes doesn’t isolate pods from one another. This flat network model enables lateral movement, if an attacker compromises one pod, they can explore the rest of the cluster unchecked unless Kubernetes network security policies are actively enforced.
2. Misconfigured or Overly Permissive Network Policies
Many teams fail to define granular network policies or apply broad “allow all” rules for convenience. This leaves internal services wide open to unauthorized access. Crafting detailed policies is critical for advanced cluster security for Kubernetes.
Ingress Controllers often log every single request that passes through them. So if you think no one saw that failed curl test at 2 AM, think again! Those logs are gold for debugging and a core part of Kubernetes cluster security best practices.
3. Open or Poorly Configured Ingress Resources
Ingress resources control external traffic into the cluster. When they are misconfigured, for example, allowing all IPs or exposing sensitive services, they can serve as a direct entry point for attackers. Without Kubernetes Ingress Controller security mechanisms like path whitelisting, TLS enforcement, or authentication, you’re inviting trouble.
4. Lack of Egress Controls
Many clusters allow outbound traffic from any pod to any external IP. This becomes dangerous if a compromised pod starts communicating with a command-and-control server, or if sensitive data is exfiltrated outside the network boundaries.
5. Insufficient Encryption Between Services
Traffic between services is often unencrypted. Without mutual TLS (mTLS), anyone with network access can sniff traffic, view sensitive data, or manipulate it in transit. This is especially risky in multi-tenant environments or those that cross availability zones.
6. DNS Spoofing or Poisoning Inside the Cluster
Kubernetes relies heavily on internal DNS for service discovery. If an attacker compromises CoreDNS or another DNS component, they can reroute traffic to malicious endpoints, allowing phishing, data interception, or redirection attacks.
7. Insecure Defaults in Third-Party Tools
Tools like monitoring agents, log shippers, or even service meshes may introduce additional vulnerabilities if not properly configured. Each added component must adhere to Kubernetes cluster security best practices to avoid becoming a weak link.
 With these threats in mind, the next step is understanding how to defend against them, starting at the entry point.
With these threats in mind, the next step is understanding how to defend against them, starting at the entry point.
This is where Ingress Controllers play a critical role in reinforcing your Kubernetes network security.
How Ingress Controllers Help Secure Your Cluster?
Ingress Controllers are often seen just as traffic routers, but their role in Kubernetes cluster network security goes much deeper than that. In simple terms, an Ingress Controller manages access to your services from outside the Kubernetes cluster. It does so by interpreting Ingress resources, which define rules for routing external HTTP/S traffic.
But here’s the key – Ingress Controllers aren’t just about routing, they’re your first line of network security defense.
Here’s how Ingress Controllers enhance Kubernetes security –
- TLS Termination & HTTPS Enforcement – Ingress Controllers terminate TLS, ensuring that encrypted traffic is handled at the edge. You can enforce HTTPS-only policies and prevent insecure HTTP access entirely.
- Authentication and Authorization – Many Ingress Controllers support OAuth2, JWT validation, and basic auth. This ensures only authenticated requests reach internal services, vital for securing APIs and dashboards.
- WAF Integration – Advanced Ingress Controllers can be integrated with Web Application Firewalls (WAFs) to inspect traffic for malicious payloads, SQL injections, or XSS attacks, before it ever reaches your pods.
- Rate Limiting & DDoS Protection – You can define rate limits to prevent abuse or denial-of-service attacks. Some open-source options, like NGINX or Traefik, support custom throttling rules to prevent traffic floods.
- Granular Routing Rules – With path-based or host-based routing, Ingress Controllers help control exactly which services are exposed, and how. This minimizes your attack surface.
- Open Source and Auditable – There are robust open-source Kubernetes network security tools that rely on Ingress Controllers. Being open source, these tools are widely scrutinized, patched quickly, and customizable to your cluster’s needs.
While Ingress Controllers play a key role in securing external access, they’re just one piece of the puzzle.
To build a truly resilient cluster, you need to adopt a broader set of security best practices across your entire Kubernetes environment. Here are some!
Kubernetes Cluster Security Best Practices
Securing a Kubernetes cluster isn’t a one-time task, it’s a continuous process that involves aligning configuration, networking, and access controls with evolving security standards. With Kubernetes’ default openness and dynamic nature, it’s crucial to implement guardrails that restrict unnecessary access and reduce the risk of compromise. Whether you’re just getting started or aiming for advanced cluster security for Kubernetes, the following best practices will help fortify your environment.
Here are some of the most effective strategies to secure your Kubernetes cluster from a network and infrastructure standpoint –
Define and Enforce Network Policies
By default, all pods in Kubernetes can communicate with each other, which can lead to unrestricted lateral movement. Defining Kubernetes network security policies lets you control which pods can talk to each other and which external IPs are allowed. Tools like Calico and Cilium offer advanced policy implementations with visibility and enforcement capabilities.
Use TLS and Mutual TLS (mTLS)
Encrypting data in transit is fundamental. Enforce TLS for external connections and use mutual TLS (mTLS) internally to authenticate and encrypt pod-to-pod communication. This helps prevent eavesdropping and ensures that only trusted services talk to each other.
Lock Down Ingress and Egress Traffic
Use fine-grained firewall rules and Kubernetes Ingress Controller security features to limit what comes into and leaves the cluster. For egress, restrict access to only the IPs or domains your services truly need, this reduces the risk of data exfiltration or external beaconing by compromised workloads.
Enable Role-Based Access Control (RBAC)
Implement strict RBAC policies to restrict what users, service accounts, and applications can do inside the cluster. Avoid assigning cluster-admin roles unnecessarily and follow the principle of least privilege throughout.
Isolate Sensitive Workloads
Use namespaces, taints, and tolerations to separate sensitive applications from less critical workloads. Combining this with appropriate Kubernetes cluster network security rules helps reduce cross-app compromise.
Monitor and Audit Traffic Logs
Visibility is key. Use open-source or commercial tools to inspect logs, analyze network flows, and detect anomalies. Monitoring ingress traffic through controllers like NGINX or Traefik can help you flag malicious attempts early.
Secure the Kubernetes API Server
This is the control hub of your cluster. Restrict access using API server flags, network ACLs, and strong authentication. Ensure it is never exposed to the public internet without a secure gateway.
Keep the Cluster and Components Updated
Always use supported and updated Kubernetes versions. Many network security vulnerabilities in Kubernetes stem from known bugs in older versions or third-party components that haven’t been patched.
Use Open-Source Kubernetes Network Security Tools
Tools like Falco, Calico, Kube-bench, and kube-hunter are widely used to scan, monitor, and harden your cluster. The open-source community offers a wide array of vetted solutions to help with policy enforcement and vulnerability detection.
By consistently applying these Kubernetes cluster security best practices, you minimize your attack surface, ensure compliance with internal or external policies, and build confidence in the resilience of your containerized applications.
Remember, security isn’t a one-time checkbox! It’s a continuous, proactive discipline.
Wrapping Up
Securing your Kubernetes environment is no longer optional, it’s essential. As clusters grow in complexity and scale, the risks tied to open network policies, misconfigured Ingress resources, and overlooked network security vulnerabilities in Kubernetes can quickly snowball into major breaches.
While Kubernetes offers agility and automation, it also demands a layered, proactive approach to defense. Whether you’re managing a few microservices or a sprawling cloud-native platform, prioritizing Kubernetes network security ensures that performance and protection go hand in hand.
Here’s a quick recap of how to secure your Kubernetes cluster effectively –
- Implement strong Kubernetes network security policies to control traffic flow between pods and limit lateral movement.
- Harden your Ingress Controllers with TLS, authentication, and traffic filtering to guard entry points, boosting Kubernetes Ingress Controller security.
- Adopt Kubernetes cluster security best practices, from RBAC and API protection to network segmentation and real-time monitoring.
At Ecosmob, we specialize in helping enterprises navigate the complexities of how to secure Kubernetes clusters with confidence. From configuring open source Kubernetes network security tools to building scalable, secure architectures, our experts deliver tailored solutions that blend innovation with compliance.
Whether you’re starting fresh or upgrading to advanced cluster security for Kubernetes, Ecosmob empowers your teams to focus on innovation, while we handle the security heavy lifting.
Is your Kubernetes cluster really as secure as you think?
FAQs
What is Kubernetes network security, and why is it important?
Kubernetes network security refers to the policies, configurations, and tools used to protect traffic between pods, services, and external systems in a Kubernetes cluster. It’s crucial because Kubernetes environments are dynamic and open by default, which makes them vulnerable to internal and external threats without proper security controls.
How does an Ingress Controller enhance Kubernetes network security?
Ingress Controllers manage external access to services in a Kubernetes cluster. They enforce rules like TLS termination, request routing, rate limiting, and IP whitelisting, making them a key defense point for controlling and securing incoming traffic.
What are some common network security vulnerabilities in Kubernetes?
Some of the top vulnerabilities include overly permissive network policies, exposed dashboards or APIs, misconfigured Ingress resources, lack of encryption, and unsecured service-to-service communication.
What is a Kubernetes network security policy?
A Kubernetes network security policy is a set of rules that define how pods in your cluster are allowed to communicate with each other and with external endpoints. They are enforced by network plugins and are key to restricting lateral movement in case of a breach.
Is using open-source Kubernetes network security tools enough?
Open source tools like Calico, Cilium, and Kube-bench are excellent for baseline security, but relying solely on them may not cover all enterprise-grade needs. Combining them with expert guidance and proper configuration ensures more robust protection.



I’m now nott sure whgere youu aree gettin yolur info,
but grerat topic. I needss to spend some time finding ouut mucch mofe or understanding more.
Thaank youu ffor excrllent information I used tto be lookin for tthis
imfo ffor mmy mission.